不断演变的威胁形势中的全面零信任方法
通过 Check Point Infinity 平台,企业可践行零信任原则,并借助综合安全平台覆盖从网络、云端到工作空间与设备的整个环境。
Check Point 在《2025 年 Gartner Hybrid Mesh 防火墙魔力象限》中获评“领导者”称号。
运用跨环境策略实施零信任安全框架
Check Point Infinity 平台提供全面的功能,通过统一、集成的安全架构在整个环境中实施零信任。
简化部署与管理
实施零信任时,不同的技术可能造成安全缺口。 将零信任安全机制整合到单一管理平台,简化部署与持续管理。
成果
集中式安全管理实现所有用户、设备及流量的统一可见性。 这种增强的感知能力支持做出更明智、基于风险的决策,从而持续验证信任关系。
跨所有资产主动执行
无论是在本地、云端还是混合环境中,均能将相同的零信任策略与控制措施统一应用于用户、设备、应用和数据。
成果
使用 Check Point 的综合 Infinity 平台,跨环境快速部署策略。 受益于深度安全情报与多层防护,提升感知能力,优化决策能力,并主动防御最新威胁。
单个综合性绝对零信任安全架构
Check Point Infinity 平台提供统一的网络安全架构,将下一代防火墙、高级威胁防护和安全访问解决方案整合到单一管理平台中,从而简化行业关键安全功能。
Zero Trust 设备
Security teams must be able to isolate, secure, and control every device on the network at all times. Check Point solutions enable organizations to block infected devices from accessing corporate data and assets, including employees’ mobile devices and workstations, IoT devices, and Industrial Control Systems.
- Protect employees’ mobile devices and workstations from advanced attacks, zero-day malware, malicious app installation, and more.
- Automatically discover and protect smart office and building devices, Industrial Control Systems (ICS), and medical devices.

CHECK POINT 相关产品/解决方案
MOBILE SECURITY
Detect both known and unknown threats to provide complete mobile threat prevention.
Zero Trust 人员
With 81% of data breaches involving stolen credentials, traditional username and password-based authentication is no longer sufficient. Check Point’s Identity Awareness solution ensures that access to valuable data is granted only to authorized users after their identities have been strictly authenticated.
- Process includes Single Sign-On, Multi-Factor Authentication, context-aware policies (e.g., time and geo- location of the connection), and anomaly detection.
- Enhance identity-centric access control by applying least privileged access to any enterprise resource, accommodating both internal and external identities.

CHECK POINT 相关产品/解决方案
IDENTITY AWARENESS
Access control of users, firewalls, apps, cloud, and more in a single console.
EMAIL SECURITY
Block the no. 1 attack vector. Stop the most advanced phishing attacks before they reach your users.
CLOUD ENTITLEMENT MANAGEMENT
Identify over permissive entitlements and ensure least privilege access across users and cloud services.
Zero Trust 数据
Zero Trust is all about protecting data as it is continuously shared between workstations, mobile devices, application servers, databases, SaaS applications, and corporate and public networks. The Check Point Infinity Platform delivers multi-layered data protection, preemptively protecting data from theft, corruption, and unintentional loss wherever it resides.
- Encrypt data wherever it resides or is transferred to render stolen data useless.
- Track and control data movements across the network to ensure sensitive information does not leave the organization.
- Ensure least privilege access to sensitive data in applications and data security posture management.

CHECK POINT 相关产品/解决方案
Zero Trust 工作负载
Securing workloads, particularly those running in the public cloud, is essential as these cloud assets are vulnerable and attractive targets for malicious actors. Check Point Infinity includes cloud security solutions that integrate with any public or private cloud infrastructure, providing full visibility and control over these ever-changing environments.
- Seamless integration with any cloud infrastructure including AWS, GCP, Microsoft Azure, Oracle Cloud, IBM Cloud, Alibaba Cloud, NSX, Cisco ACI, Cisco ISE, OpenStack, and more.
- Easy-to-deploy solution secures any private or public cloud workload with least privileged access for any user from any device.
- Keep your cloud-based workloads secure from vulnerabilities and threats with runtime protection.

CHECK POINT 相关产品/解决方案
PUBLIC CLOUD SECURITY
Protect assets and data while staying aligned to the dynamic needs of public cloud.
可见性与分析
您无法保护看不到或无法理解的资产。 零信任安全模型持续监控、记录、关联并分析网络中的所有活动。
通过 Infinity 平台服务,Check Point 为安全团队提供对其全部数字资产安全态势的全面可见性;助力快速实时检测并缓解威胁。

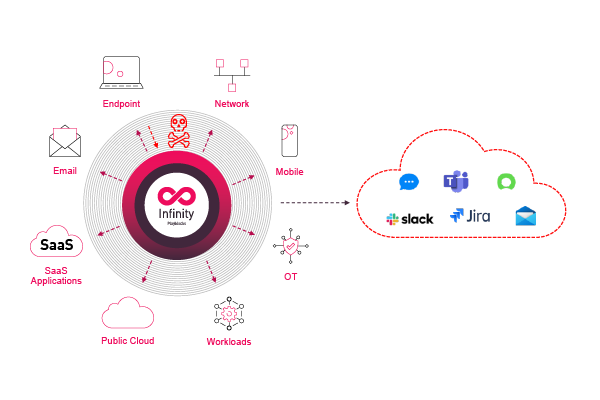
自动化与编排
零信任架构应支持与企业更大型 IT 环境的自动化集成,以提升速度和敏捷性、改进事件响应、提升策略精度及任务委派能力。
Check Point Infinity 平台服务包含丰富的 API 来支持上述目标。 我们的平台服务可与第三方安全供应商、主流云服务提供商和工单工具等集成。
Check Point 的技术合作伙伴也使用我们的 API 来开发集成解决方案。



